One of the big drivers for investment in open source tooling is security. We want to introduce you to Dependabot - a tool you should probably be using to help you keep your open source components up to date.
About Dependabot
Dependabot is an automated system built into Github that tracks updates to the packages your project is using. It automatically creates issues when your dependencies go out of date, especially highlighting changes that are security-related.
Dependabot started as a Github-exclusive functionality, but the core is open source. It has an active port to Gitlab that is kept updated.
Security - and compliance - throughout the supply chain
Dependabot is used to help you with your open source supply chain. When working on your own products, you can't just look at the vulnerabilities in your own application. Your application is also a consumer of many other open source libraries. Each of those libraries has its own supply chain that needs to be managed.
More specifically, a typical open source project will incorporate a large number of third party components. Due to the evolving nature of software, it is only natural that some of those components will accumulate security alerts.
Dependabot shows you those transitive dependencies. This allows you to be aware of both vulnerabilities as well as licensing issues throughout your supply chain.
How does Dependabot work?
Dependabot tracks recommended upgrades against the dependencies identified in the project and presents maintainers with a list of recommended upgrades. It does this for a project's direct dependencies as well as for the dependencies of the dependencies. Sometimes the chain can go six, seven, or eight levels deep.
Some of these upgrades can be handled automatically, particularly if there is a good test suite that gives you confidence that the change won't cause any problems. There are extensions that allow simple changes to be automatically merged.
Be aware that many of the updates need to be manually reviewed. Projects change. Even more difficult, sometimes there are version incompatibilities between dependencies.
Getting started with Dependabot
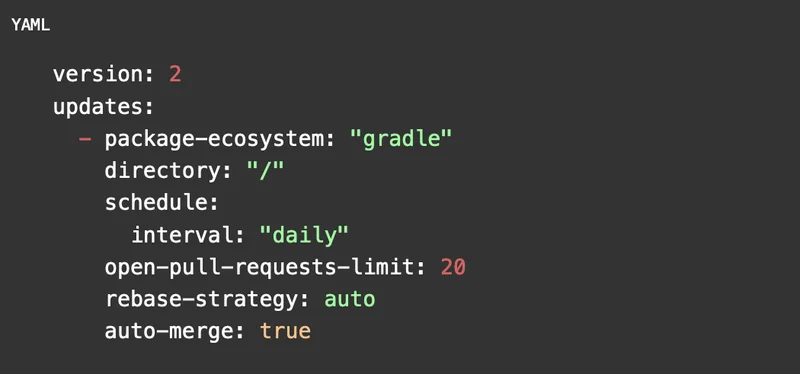
When getting started with Dependabot you may want to begin with a few trial deployments. Any repositories that wish to receive automated dependency update merge requests will need to be configured through a dependabot.yml file. It has a few options that allow it to integrate with various systems. For example, for a Gradle project your configuration file might look something like this:
As you become more used to Dependabot, you can add more repositories.
Be prepared for volume
As you roll out Dependabot, be aware that it will surface many more issues than you might have realized you had. Sometimes the number of changes that need to be managed can seem overwhelming. But a little dedicated time, those Dependabot requests can be managed and your project will be safer for it.
You can't tool yourself out of a job
At OSPOCO, we like Dependabot and we strongly recommend it for our clients. Unfortunately, however, Dependabot is just a tool that we use. It doesn't replace the need to engage with external contributors and communities.
Let me make the issue more concrete. In one case, a client project had three dependencies - A, B, and C. Each of those dependencies ended up sharing a common dependency, D, that had a reported security vulnerability.
One project - A - had incorporated the fix and was ready for the upgrade. In contrast, projects B and C had a "pin" to the vulnerable version. That means that their code incorporated declarations that it was incompatible with anything but a specific version of the dependency D.
The result was that if we upgraded the dependency D to the non-vulnerable version, two of our three dependencies would break.
Fixing problems like this isn't as much of a technical issue as it is a people issue.
The solution was to go to the maintainers of projects B and C and submit fixes that allowed them to use the updated version of D. Once those upstream projects were fixed, we were able to flow that change down into the client's code.
Check it out
If you use Github, Dependabot is already available for you. If you run Gitlab or something else, you will need to do some manual deployment and configuration. The time put into configuring and managing Dependabot issues will be time well spent.